Network Level Authentication, or NLA, is a core component of any support protocol. Used effectively, it can make your environment more secure. Want to know the basics about NLA? Let's dive in.
What is NLA?
Let's start with the basics.Network-level authentication authenticates Remote Desktop services, such as Remote Desktop Connection (RDP Client) andWindows RDP. It’s also referred to as front authentication because it requires the end user to enter their credentials to make the session work.NLA is a Remote Desktop Services (RDP Server) feature requiring the connecting user to authenticate themselves prior to a session being established with the server.
Before NLP, if a user opened a remote desktop session to a server, the login screen from the server for the user would load. This would use up precious resources on the server and was a potential weak spot for remote code execution attacks and denial of service. Not good.
Enter NLA, which delegates the user's credentials from the client through a client-side security support provider prompting the user to authenticate before establishing their session with the server. Much better for user experience and so much safer.
NLA was first introduced in RDP 6.0, supported initially in Windows Vista. It uses Security Support Provider CredSSP, which is available through SSPI in Windows Vista (remember Vista - or are you like us and trying to pretend that we went straight from XP to 7?). CredSSP was introduced with XP Service Pack 3, and that included RDP 6.1 client supported NLP; however, admins had to enable CredSSP in the registry first.
What is NLA used for?
NLA is a simple and safe way for users to authenticate themselves before initiating a remote desktop session.
How to enable NLA?
As we discussed previously, NLA isn't enabled by default, so here's how to switch it on. You can do this in multiple ways, including:
Settings
System settings
Enabling NLA via settings
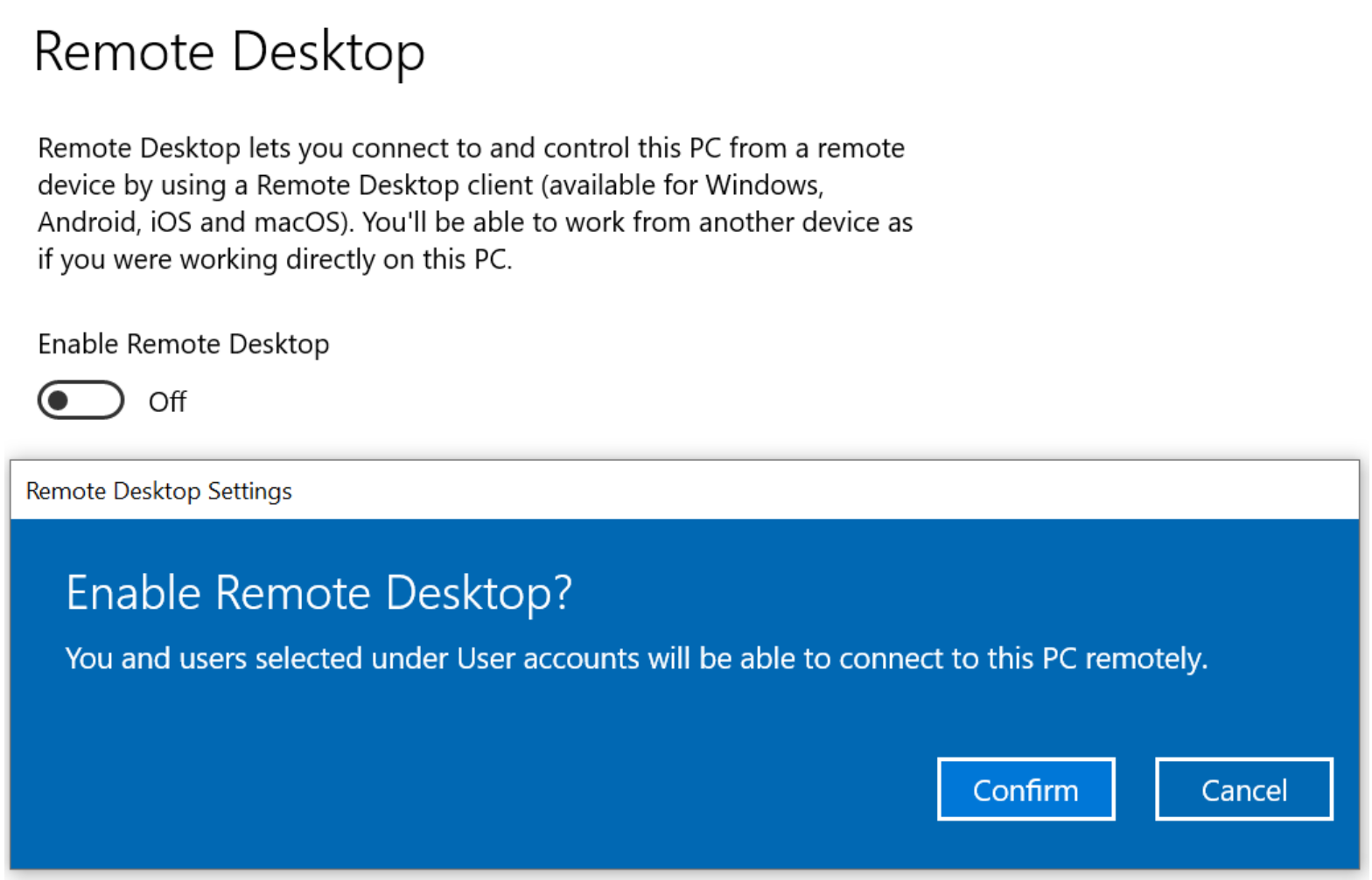
The first option you have is to go toSettings in your Start menu, search forRemote Desktop, then selectEnable Remote Desktop radio button.
Click theAdvanced Settings button to ensure the required computers for Network Level Authentication are checked.It's also recommended to keep the PC awake and discoverable to enable connections. ClickShow settings to enable this.
The control panel method. You can also enable NLA via the Control Panel of your machine. Fire up Control Panel, click System and Security,followed by theAllow Remote Access option. Click onRemote,Remote Desktop, and there you'll see an option namedAllow remote connections to this computer. Make sure you select theAllow connections only from computers running Remote Desktop with Network Level Authentication setting.
Different versions of Windows. Setting up for NLA can look slightly different depending on which version of Windows you're operating, for example:
Windows 10Fall Creators update (1709) or above.You can use the above ways, and a separate downloadable app provides similar functionality for earlier versions of Windows. There’s also the option of using the legacy way of enabling Remote Desktop; but this method offers less functionality and validation.
Windows 7 and early versions of Windows 10. Download and run the Microsoft Remote Desktop Assistant, which will update your system settings to ensure your computer is awake for connections, to allow remote access,and to check that your firewall allows Remote Desktop connections. In short, it does all the heavy lifting for you!
Older version of Windows (aka the legacy method). To enable Remote Desktop using legacy system properties, you need tofollow these instructions to connect to another computer using Remote Desktop Connectionon the Microsoft support site.
What are the benefits of NLA?
NLA has several benefits, including:
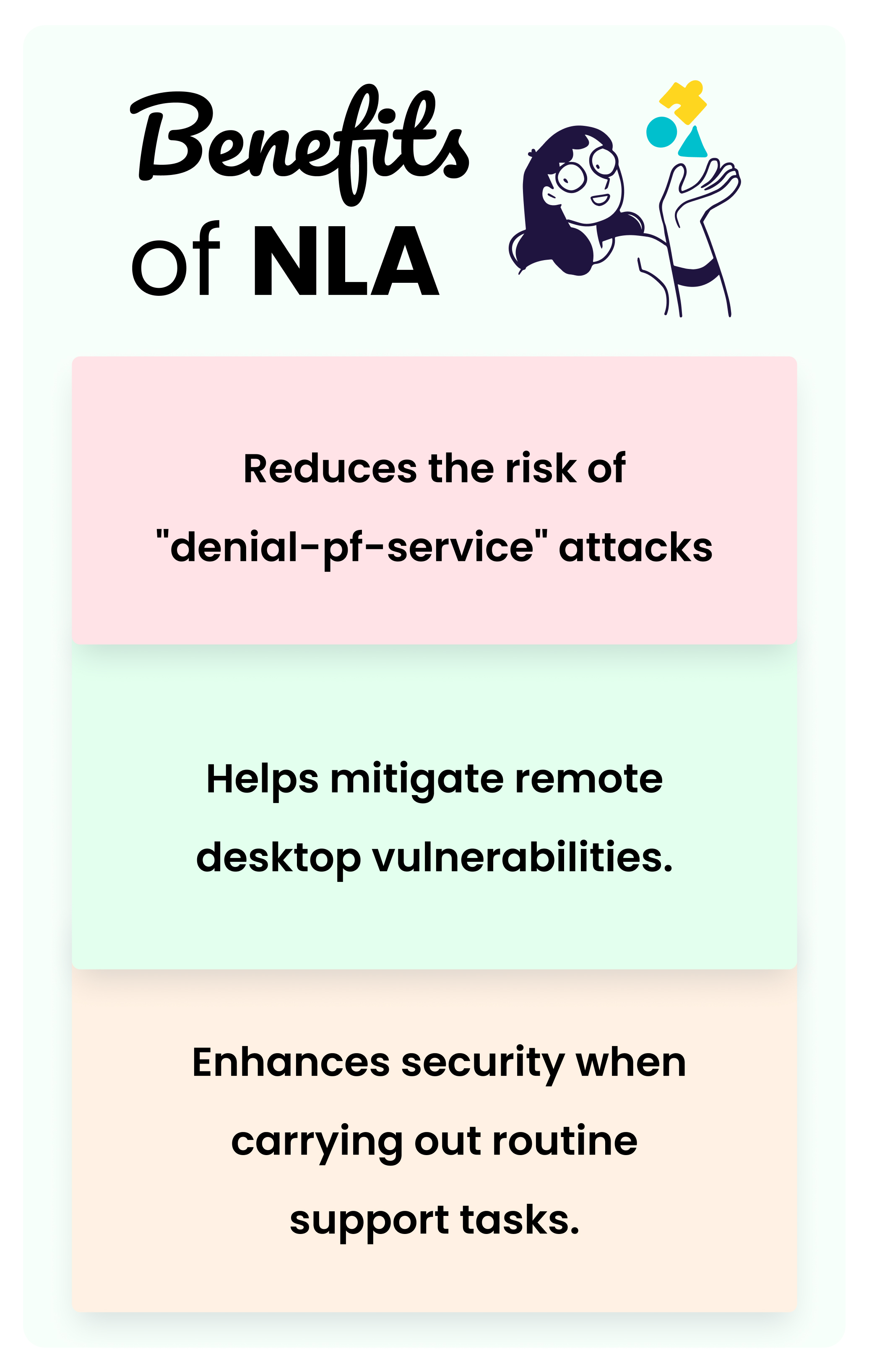
It initially requires fewer remote computer resources by preventing the initiation of a complete remote desktop connection until the user is authenticated, which reduces the risk of denial-of-service attacks.
It helps to mitigate Remote Desktop vulnerabilities, which can only be exploited prior to authentication.
It allows NT Single sign-on (SSO), extending to Remote Desktop Services.
It prompts techs and sysadmins to consider security when carrying out routine support tasks.
Remote Desktop with NLA
So, how do you use Remote Desktop with NLA? Here are our top 3 tips:
Check the end user:First and foremost, check that the machine the end user is working on can support NLA because if working in tech support for years has taught us anything, you just never know. The easiest way is to ask your user to start the Remote Desktop Connection in the way that is best for them. Our preferred way of asking is going, "OK, what you're going to do is hit the Windows key and type in the word remote. Something called Remote Desktop Connection will appear on your screen. Just click that and we can go from there." Once they have it open, look in the top left-hand corner of the RDC dialog box, and there will be an option that saysAbout. In theAbout Remote Desktop Connection dialog box, there should be a mention of Network Level Authentication supported, which will confirm that NLA is supported on the device.
The end user experience: Once you've established that NLA is supported, tell the end user what to expect. You’ll need to explain that a message will pop up when the remote desktop connection is made so the user can authenticate before the connection is established. It's worth spending time explaining this because nothing spooks an end user like an unexpected message popping up. This authentication requirement provides additional security that will make the session safer - the client's credentials will be requested, and the session will only start once the credentials are approved.
Ace your prep work:To connect to a remote PC, the computer must be switched on with a network connection. Remote Desktop must be enabled, you need to have permission to connect, you need network access to the remote computer (potentially via the internet), and you have to be on the list of users for permission to connect. Before you initiate a connection, it's useful to look up the name of the computer that you're connecting to and to ensure Remote Desktop connections are allowed through its firewall