Last Updated : 19 Jun, 2024
Summarize
Comments
Improve
User Datagram Protocol (UDP) is a Transport Layer protocol. UDP is a part of the Internet Protocol suite, referred to as UDP/IP suite. Unlike TCP, it is an unreliable and connectionless protocol. So, there is no need to establish a connection before data transfer.The UDP helps to establish low-latency and loss-tolerating connections over the network. The UDP enables process-to-process communication.
What is User Datagram Protocol?
User Datagram Protocol (UDP) is one of the core protocols of the Internet Protocol (IP) suite. It is a communication protocol used across the internet for time-sensitive transmissions such as video playback or DNS lookups. Unlike Transmission Control Protocol (TCP), UDP is connectionless and does not guarantee delivery, order, or error checking, making it a lightweight and efficient option for certain types of data transmission.

UDP Header
UDP header is an 8-byte fixed and simple header, while for TCP it may vary from 20 bytes to 60 bytes. The first 8 Bytes contain all necessary header information and the remaining part consists of data. UDP port number fields are each 16 bits long, therefore the range for port numbers is defined from 0 to 65535; port number 0 is reserved. Port numbers help to distinguish different user requests or processes.
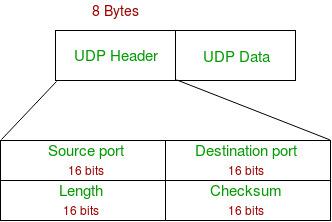
UDP Header
- Source Port: Source Port is a 2 Byte long field used to identify the port number of the source.
- Destination Port: It is a 2 Byte long field, used to identify the port of the destined packet.
- Length: Length is the length of UDP including the header and the data. It is a 16-bits field.
- Checksum: Checksum is 2 Bytes long field. It is the 16-bit one’s complement of the one’s complement sum of the UDP header, the pseudo-header of information from the IP header, and the data, padded with zero octets at the end (if necessary) to make a multiple of two octets.
Notes – Unlike TCP, the Checksum calculation is not mandatory in UDP. No Error control or flow control is provided by UDP. Hence UDP depends on IP and ICMP for error reporting.Also UDP provides port numbers so that is can differentiate between users requests.
Applications of UDP
- Used for simple request-response communication when the size of data is less and hence there is lesser concern about flow and error control.
- It is a suitable protocol for multicasting as UDP supports packet switching.
- UDP is used for some routing update protocols like RIP(Routing Information Protocol).
- Normally used for real-time applications which can not tolerate uneven delays between sections of a received message.
- VoIP (Voice over Internet Protocol) services, such as Skype and WhatsApp, use UDP for real-time voice communication. The delay in voice communication can be noticeable if packets are delayed due to congestion control, so UDP is used to ensure fast and efficient data transmission.
- DNS (Domain Name System) also uses UDP for its query/response messages. DNS queries are typically small and require a quick response time, making UDP a suitable protocol for this application.
- DHCP (Dynamic Host Configuration Protocol) uses UDP to dynamically assign IP addresses to devices on a network. DHCP messages are typically small, and the delay caused by packet loss or retransmission is generally not critical for this application.
- Following implementations uses UDP as a transport layer protocol:
- NTP (Network Time Protocol)
- DNS (Domain Name Service)
- BOOTP, DHCP.
- NNP (Network News Protocol)
- Quote of the day protocol
- TFTP, RTSP, RIP.
- The application layer can do some of the tasks through UDP-
- Trace Route
- Record Route
- Timestamp
- UDP takes a datagram from Network Layer, attaches its header, and sends it to the user. So, it works fast.
TCP vs UDP
| Basis | Transmission Control Protocol (TCP) | User Datagram Protocol (UDP) |
|---|---|---|
| Type of Service | TCPis a connection-oriented protocol. Connectionorientation means that the communicating devices should establish a connection before transmitting data and should close the connection after transmitting the data. | UDPis the Datagram-oriented protocol. This is becausethere is no overhead for opening a connection, maintaining a connection, or terminating a connection. UDP is efficient for broadcast and multicast types of network transmission. |
| Reliability | TCP is reliable as it guarantees the delivery of data to the destination router. | The delivery of data to the destination cannot be guaranteed in UDP. |
| Error checking mechanism | TCP provides extensive error-checking mechanisms.It is because it provides flow control and acknowledgment of data. | UDP has only the basic error-checking mechanism using checksums. |
| Acknowledgme nt | An acknowledgment segment is present. | No acknowledgment segment. |
| Sequence | Sequencing of data is a feature of Transmission ControlProtocol (TCP). this means that packets arrive in order at the receiver. | There is no sequencing of data in UDP. If the order is required, it has to be managed by the application layer. |
| Speed | TCP is comparatively slower than UDP. | UDP is faster, simpler, and more efficient than TCP. |
| Retransmission | Retransmission of lost packets is possible in TCP, but not in UDP. | There is no retransmission of lost packets in the User Datagram Protocol (UDP). |
| Header Length | TCP has a (20-60) bytes variable length header. | UDP has an 8 bytes fixed-length header. |
| Weight | TCP is heavy-weight. | UDP is lightweight. |
| Handshaking Techniques | Uses handshakes such as SYN, ACK, SYN-ACK | It’s a connectionless protocol i.e. No handshake |
| Broadcasting | TCP doesn’t support Broadcasting. | UDP supports Broadcasting. |
| Protocols | TCP is used byHTTP, HTTPs,FTP,SMTPandTelnet. | UDP is used byDNS,DHCP, TFTP,SNMP,RIP, andVoIP. |
| Stream Type | The TCP connection is a byte stream. | UDP connection is a message stream. |
| Overhead | Low but higher than UDP. | Very low. |
| Applications | This protocol is primarily utilized in situations when a safe and trustworthy communication procedure is necessary, such as in email, on the web surfing, and inmilitary services. | This protocol is used in situations where quick communication is necessary but where dependability is not a concern, such as VoIP, game streaming, video, and music streaming, etc. |
Advantages of UDP
- Speed: UDP is faster than TCP because it does not have the overhead of establishing a connection and ensuring reliable data delivery.
- Lower latency: Since there is no connection establishment, there is lower latency and faster response time.
- Simplicity: UDP has a simpler protocol design than TCP, making it easier to implement and manage.
- Broadcast support: UDP supports broadcasting to multiple recipients, making it useful for applications such as video streaming and online gaming.
- Smaller packet size: UDP uses smaller packet sizes than TCP, which can reduce network congestion and improve overall network performance.
- User Datagram Protocol (UDP) is more efficient in terms of both latency and bandwidth.
Disadvantages of UDP
- No reliability: UDP does not guarantee delivery of packets or order of delivery, which can lead to missing or duplicate data.
- No congestion control: UDP does not have congestion control, which means that it can send packets at a rate that can cause network congestion.
- Vulnerable to attacks: UDP is vulnerable to denial-of-service attacks, where an attacker can flood a network with UDP packets, overwhelming the network and causing it to crash.
- Limited use cases: UDP is not suitable for applications that require reliable data delivery, such as email or file transfers, and is better suited for applications that can tolerate some data loss, such as video streaming or online gaming.
How is UDP used in DDoS attacks?
AUDP flood attackis a type ofDistributed Denial of Service (DDoS)attack where an attacker sends a large number ofUser Datagram Protocol (UDP)packets to a target port.
- UDP Protocol: Unlike TCP, UDP is connectionless and doesn’t require a handshake before data transfer. When a UDP packet arrives at a server, it checks the specified port for listening applications. If no app is found, the server sends anICMP “destination unreachable”packet to the supposed sender (usually a random bystander due to spoofed IP addresses).
- Attack Process:
- The attacker sends UDP packets with spoofed IP sender addresses to random ports on the target system.
- The server checks each incoming packet’s port for a listening application (usually not found due to random port selection).
- The server sends ICMP “destination unreachable” packets to the spoofed sender (random bystanders).
- The attacker floods the victim with UDP data packets, overwhelming its resources.
- Mitigation: To protect against UDP flood attacks, monitoring network traffic for sudden spikes and implementing security measures are crucial. Organizations often use specialized tools and services to detect and mitigate such attacks effectively.
UDP Pseudo Header
- The purpose of using a pseudo-header is to verify that the UDP packet has reached its correct destination
- The correct destination consist of a specific machine and a specific protocol port number within that machine

UDP pseudo header
UDP Pseudo Header Details
- The UDP header itself specify only protocol port number.thus , to verify the destination UDP on the sending machine computes a checksum that covers the destination IP address as well as the UDP packet.
- At the ultimate destination, UDP software verifies the checksum using the destination IP address obtained from the header of the IP packet that carried the UDP message.
- If the checksum agrees, then it must be true that the packet has reached the intended destination host as well as the correct protocol port within that host.
User Interface
A user interface should allow the creation of new receive ports, receive operations on the receive ports that returns the data octets and an indication of source port and source address, and an operation that allows a datagram to be sent, specifying the data, source and destination ports and address to be sent.
IP Interface
- The UDP module must be able to determine the source and destination internet address and the protocol field from internet header
- One possible UDP/IP interface would return the whole internet datagram including the entire internet header in response to a receive operation
- Such an interface would also allow the UDP to pass a full internet datagram complete with header to the IP to send. the IP would verify certain fields for consistency and compute the internet header checksum.
- The IP interface allows the UDP module to interact with the network layer of the protocol stack, which is responsible for routing and delivering data across the network.
- The IP interface provides a mechanism for the UDP module to communicate with other hosts on the network by providing access to the underlying IP protocol.
- The IP interface can be used by the UDP module to send and receive data packets over the network, with the help of IP routing and addressing mechanisms.
GATE Questions for Practice
- GATE CS 2013, Question 12
- GATE CS 2012, Question 65
- GATE CS 2007, Question 20
- GATE CS 2005, Question 23
- GATE IT 2008, Question 66
- GATE Mock 2015, Question 5
Conclusion
The User Datagram Protocol (UDP) is an important Transport Layer protocol in the Internet Protocol (IP) suite, identified for its speed and efficiency due to its connectionless and lightweight design. While UDP lacks TCP’s stability and error-checking features, it used in applications that need low latency and real-time performance, such as streaming, online gaming, and DNS lookups. Its simplicity and support for broadcast and multicast broadcasts make it a useful tool for specialized applications, despite its vulnerability to data loss and network congestion.
Frequently Asked Questions on UDP – FAQs
Name the protocols that uses UDP?
The protocol that uses UDP Model are:
- Domain Name System(DNS)
- Simple Network Management Protocol(SMTP)
- Routing Information Protocol(RIP)
Which is faster: TCP or UDP?
UDP is faster than TCP.
Is UDP secure?
Yes UDP provide various security mechanism.
Is UDP a layer 3 or 4?
UDP is layer 4 protocol of OSI Model
Previous Article
TCP/IP Model
Next Article
Difference Between IPv4 and IPv6

